
PEW PEW HACKING YOUR FRIEND BLUETOOH CONVERSATION AND LOGGING ALL YOUR EARPHONE … . EXPLOIT CODE BY SKRAITO WITH SKRAITOW ( LORD JESUS CHRIST ) … .
PEW PEW – PoC to record audio from a Bluetooth device
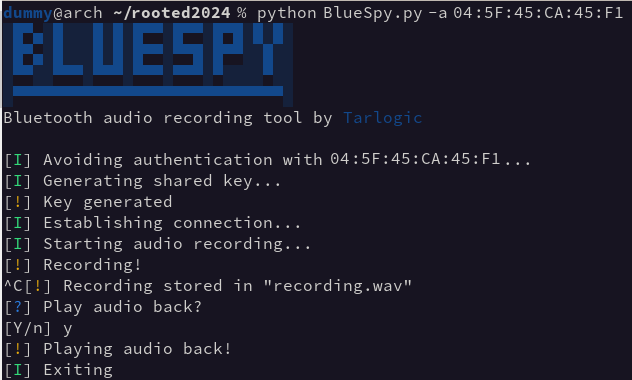
proof of concept to record and replay audio from a bluetooth device without the legitimate user’s awareness.
Requirements
The code is written in Python and has been tested with Python 3.11.8, but it mainly uses widely available tools in Linux systems.
The PoC uses the following tools:
bluetoothctlbtmgmtpactlparecordpaplay
In Arch Linux distributions, bluetoothctl and btmgmt can be installed with the package bluez-utils, while pactl, parecord and paplay are available in the libpulse package.
For the PoC to work, it is necessary to have a working installation of the BlueZ Bluetooth stack, available in the bluezpackage for Arch Linux distributions. A working installation of an audio server compatible with PulseAudio, such as PipeWire, is also required to record and play audio.
Setup
Ensure that your device is capable of functioning as an audio source, meaning it has a microphone, and that it is discoverable and connectable via Bluetooth.
For instance, to be discoverable and connectable, the earbuds used during the talk must be outside of their charging case. By default, they only activate the microphone when placed in the user’s ears, although this setting can be adjusted in the configuration app.
Additionally, ensure that the device is not already connected, or alternatively, that it supports multiple connections.
Execution
Firstly, the address of the device must be discovered using a tool such as bluetoothctl:
$ bluetoothctl
[bluetooth]# scan on
Once the address of the device is discovered, the script can handle the rest:
$ python BlueSpy.py -a <address>
Note: The script might prompt for superuser permissions to modify the configuration of your BlueZ instance and pair it with the remote device.
Troubleshooting
BlueSpy.py is the main script that executes every step of the process. However, if you encounter issues with any of the phases, so it might be helpful to execute them individually:
pair.pyutilizes the command-line toolbtmgmtto modify the configuration of your BlueZ and initiate a pairing process with the remote device. The exact commands used are in thepairfunction insidecore.py.connect.pyutilizes the command-line toolbluetoothctlto initiate a quick scan (necessary for BlueZ) and establish a connection to the device. The exact commands used are in theconnectfunction insidecore.py.just_record.pyutilizes the command-line toolspactlandparecordto search for the device in the system’s audio sources (it must function as a microphone) and initiate a recording session. The exact commands used are in therecordfunction insidecore.py.- The
playbackfunction insidecore.pyexecutespaplayto play back the captured audio.
If you encounter issues with any of the phases, examine the commands in core.py and try to execute them in a shell. This will provide more information on what may be failing.
https://www.worldhacker.org/download-0day.xc.Our.license.apply/pewpew.bluetoohsniffer.zip
You may also like
Archives
Categories
- 0day
- 0day Anime Watch Online
- AI Secret
- AntiVirus Evasion Technique
- Blackcat Anime
- Crayon Sinchan
- Demon School! Iruma-kun
- Donald Duck And Friend
- Dr. Stone Season 1
- Dr. Stone Season 2
- Exploit-0day
- Fairy Tail
- God and Christianity
- How Everything Work PHD Thesis
- Hunter X Hunter
- PHD THESIS
- Project
- Public-Release-Code
- Ragna Crimson
- Rurouni Kenshin -Kyoto Disturbance-
- Security Tutorial
- The Seven Dealy Sins
- Uncategorized
- World Game By Us
- World Havoc Tarif
- World Tarif Secret
- WormGPT
Leave a Reply