[ 0day (xc) Our ] Proof Of Concept SSL AND TLS HACKING MAN IN THE MIDDLE ATTACK BY SKRAITOW ( LORD JESUS CHRIST ) WITH SKRAITO … .
The new PewPew attack is a sophisticated cross-protocol application layer desynchronization vulnerability that compromises TLS-based communications.
This attack exploits fundamental differences between implicit and opportunistic TLS implementations, affecting critical protocols including HTTP, FTP, POP3, SMTP, LMTP, and NNTP.
By leveraging man-in-the-middle positioning, attackers can inject unexpected messages into secure channels, causing persistent desynchronization between clients and servers and breaking the integrity assumptions of encrypted communications.
Attack Exploits TLS Authentication
The PewPew attack represents a sophisticated evolution of protocol-level vulnerabilities that target the authentication mechanisms within TLS implementations.
This cross-protocol desynchronization attack specifically exploits services supporting both implicit TLS (dedicated secure ports) and opportunistic TLS (plaintext-to-encrypted upgrade mechanisms) simultaneously.
The attack builds upon the foundational weaknesses identified in the ALPACA attack while introducing novel exploitation vectors that circumvent existing countermeasures.
The vulnerability affects protocols where subtle differences exist between implicit and opportunistic TLS variants after the handshake completion.
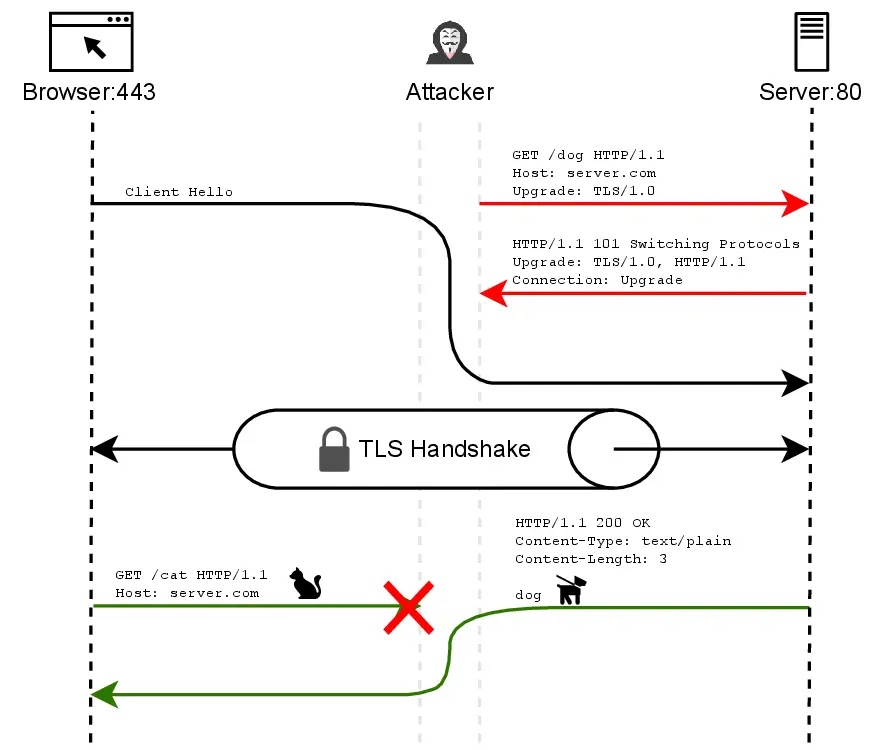
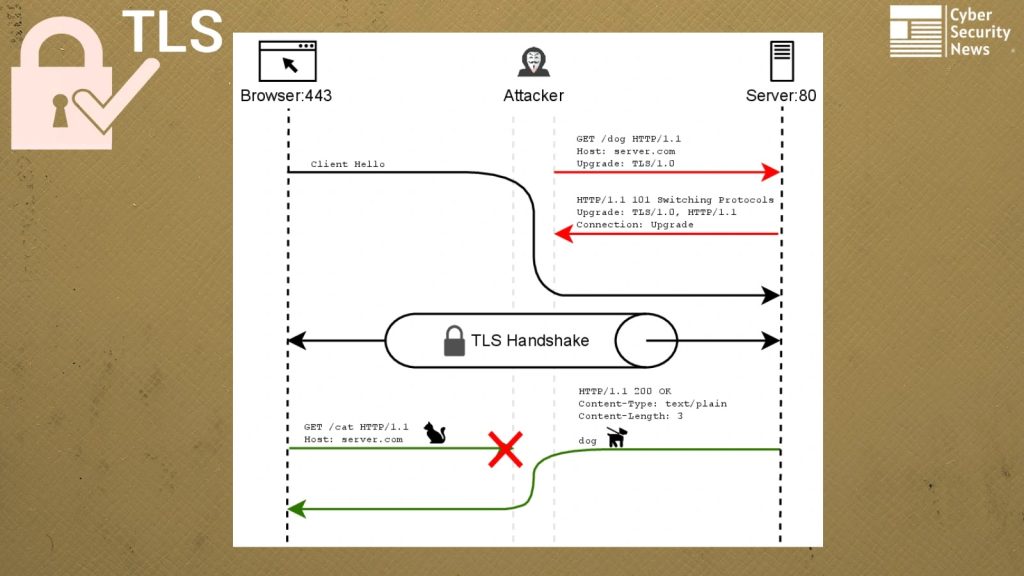
When a client attempts a connection using one method, attackers can redirect traffic to utilize the alternative method, creating critical mismatches in protocol expectations.
This application layer desynchronization persists throughout the connection lifecycle, enabling sustained manipulation of client-server communications.
The technical execution of PewPew involves intercepting client connections intended for implicit TLS endpoints and redirecting them through opportunistic TLS channels.
For HTTP implementations, attackers intercept HTTPS traffic destined for port 443 and establish plaintext connections to port 80 with TLS upgrade headers. A simple vulnerability test can be performed using:
If the server responds with “101 Switching Protocols”, it supports RFC 2817 TLS upgrade functionality and remains vulnerable.
The attack manipulates the ALPN (Application Layer Protocol Negotiation) strings and exploits timing differences in protocol state machines.
After TLS handshake completion, simultaneous message transmission creates persistent desynchronization where clients receive incorrect responses to their requests.
The vulnerability affects all TLS versions, including TLS 1.3, since it exploits protocol integration rather than cryptographic implementations.
Apache servers can be configured vulnerably using the SSLEngine option, demonstrating the widespread applicability of this attack vector across different server implementations.
Mitigations
PewPew enables multiple attack classes in HTTPS contexts, including resource confusion, session fixation, reflected XSS escalation, and implementation-specific vulnerabilities like cookie leakage.
Internet-wide scans identified over 3 million hosts supporting both implicit and opportunistic TLS, though practical exploitation remains limited for non-HTTP protocols.
The most effective mitigation strategy involves disabling opportunistic TLS support entirely and migrating to implicit TLS implementations. For HTTP servers, this requires disabling RFC 2817 upgrade functionality.
Vendors, including Apache Foundation (CVE-2025-49812), Cyrus IMAPD, and others, have begun implementing patches and deprecation strategies to address this vulnerability systematically.
Organizations should immediately assess their TLS configurations, disable opportunistic TLS where possible, and prioritize implicit TLS implementations to maintain secure communications integrity.
You may also like
Archives
Categories
- 0day
- 0day Anime Watch Online
- AI Secret
- AntiVirus Evasion Technique
- Blackcat Anime
- Crayon Sinchan
- Demon School! Iruma-kun
- Donald Duck And Friend
- Dr. Stone Season 1
- Dr. Stone Season 2
- Exploit-0day
- Fairy Tail
- God and Christianity
- Hunter X Hunter
- PHD THESIS
- Project
- Public-Release-Code
- Ragna Crimson
- Rurouni Kenshin -Kyoto Disturbance-
- Security Tutorial
- The Seven Dealy Sins
- Uncategorized
- World Game By Us
- World Havoc Tarif
- World Tarif Secret
- WormGPT
Leave a Reply